Hacker Methodology
Its very important to understand the hacker methodology and build security on these levels in order to protect your system or corporate network.
Many Ethical hacker names these steps with different words but overall background concept it almost same.
if you are a ethical hacker then you need to write a contract with company before performing any penetrate testing. its does not matter what level of testing you are doing but it has to be officially approved by authorised person. (wireless penetrate testing,webserver, network , System or application).
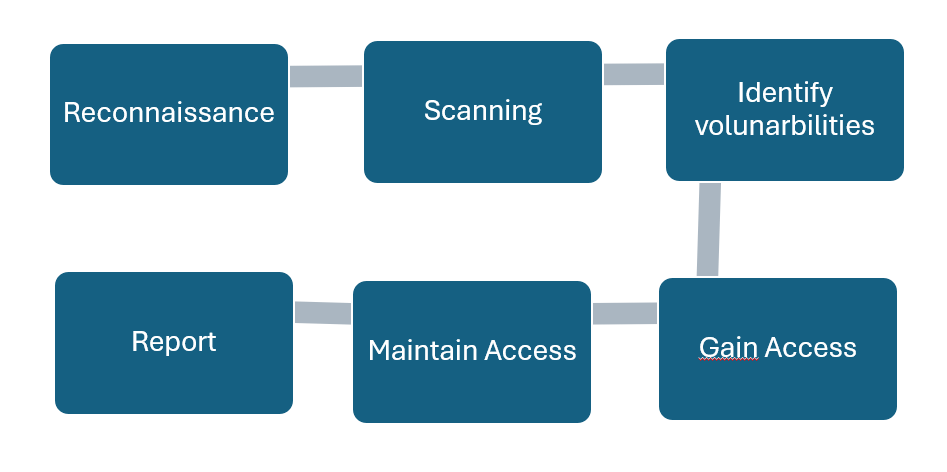
Phases of Ethichal Hacking
1. Reconnaissance : In this phase of analysis , Ethical hacker gather information about system in passive mode without giving any alert to System .
2. Scanning : Ethical hacker perform active scanning to system by using tool like Nmap (free tool), Nessus(its paid tool). there is high chance that you will alert system administrator.
3. Identify Volunerability: identify the application version or Os version used in system and find the volunerability mentioned in Rapid7 or exploitdb.com database for more details and how to exploit system
4. Gain Access : Get access to system by exploiting the open volunerabilty of system. open session with target device and get access to files, folders and sensitive informations.
5. Maintain access : this is very important phase , dangerous hacker mostly extend their access to multiple system in this phase and maintain it. it may be one system get fixed but their spread access into network system so loosing one access to system does not much affect them. being a ethical hacker its reposbilities to close these gaps for black hat hackers.
6. Report : In this final phase , Ethical hacker submit a report back to company so they can fix the risk areas.
once all the testing is completed , ethical hacker must clear all the logs and traces of penetrate testing from performed system.
follow my linked in group https://www.linkedin.com/groups/14529294/
Thanks
Webmaster

